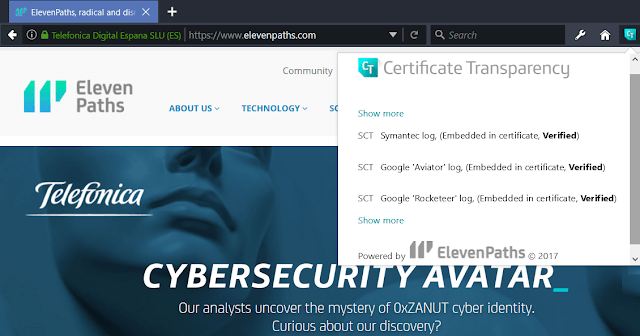
 |
| Checking the SCT embedded in our certificates |
Certificate Transparency is a new layer of security on top of TLS ecosystem. Sponsored by Google, it basically makes all the issued certificates to be logged (in some special servers), so if an eventual attacker would want to create a rogue one, it would face a dilemma: If the rogue certificate is not logged, that would rise up some eyebrows… if logged, that would allow a faster detection.
A certificate is considered “logged” if it counts with a SCT (Signed Certificate Timestamp). This SCT is given to the owner of the certificate when logged, and the browser has to verify it is real and current. This is exactly what Chrome has been doing for a while now. Now Firefox, thanks to this plugin, is able to check the SCT for certificates. But there are some good news and bad news:
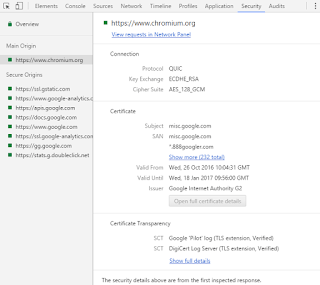 |
| This is how Chrome checks the SCT |
The good news
Our addon, created in cooperation with our lab in Buenos Aires, works with most of known logs. It means that it does not matter from which log the SCT comes from, we will be able to check it because we have introduced the public key and address of basically all known logs so far:
Google ‘Pilot’, Google ‘Aviator’, DigiCert Log Server, Google ‘Rocketeer’, Certly.IO, Izenpe, Symantec, Venafi, WoSign, WoSign ctlog, Symantec VEGA, CNNIC CT, Wang Shengnan GDCA , Google ‘Submariner’, Izenpe 2nd, StartCom CT, Google ‘Skydiver’, Google ‘Icarus’ , GDCA, Google ‘Daedalus’, PuChuangSiDa, Venafi Gen2 CT, Symantec SIRIUS and DigiCert CT2.
This makes our solution quite complete but…
The bad news
SCT may be delivered by three different ways:
- Embedded in the certificate.
- As a TLS extension.
- In OCSP.
It is not easy from a plugin technical perspective to get to TLS or OCSP extensions layer and check the SCT. So our plugin so far checks for SCT embedded in the certificate itself. Although not ideal, this is the most common scenario so most of certificates distribute its SCT embedded.
Another bad news is that plugins have to be validated by Mozilla to be published in its addons store. Once uploaded the plugin gets in a queue. If it contains “complex code” it may be there for longer, so Mozilla can make a better work reviewing and checking its security and quality. After waiting for more than two months, we have decided not to wait anymore. The queue seems to be stuck for days and days and the is no hope to make it work faster. Mozilla reviewers are working as much as they can, but they can not deal with so many addons as fast as they would like to. We thank them anyway. That is why we have decided to distribute it outside addons store. Once it gets reviewed released, we will let you know.
The addon is available from here.
To install it, just drag and drop the file into a new tab.
Or, from the extensions menu, settings, install from a file.
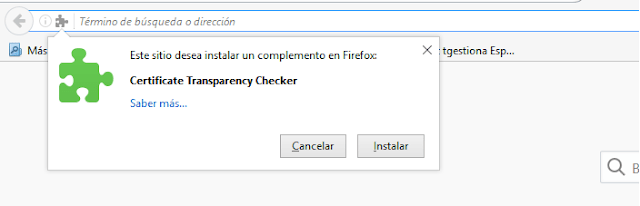






is an option?
thor the,,,
This is just the information I am finding everywhere. Thanks for your blog, I just subscribe your blog. This is a nice blog.. Search Bar Firefox 57 Quantum addon
According to OneStat the usage of Firefox has risen to 11.51 % globally. We wil try to find out what has led so many users to switch to Firefox. firefox 57 quantum
Try Search Bar Firefox 57 Quantum addon to get quick results, and have a great net surfing experience.