Malware industry needs to improve and keep on stealing. So they research and invest. There are two different ways of investing if you are “in the business”: one is investing in new vulnerabilities so you can infect more efficiently. This is complex and will not talk about that in this post. The other side to invest in, is how to steal more efficiently once the victim is infected. What have they done about it lately?
Which is the most lucrative banking trojan?
There are millions of banking trojans. More that you can probably imagine, and more than the antivirus companies can handle. But most of them have quite a lot in common. Basically in their targets (stealing, the more the better) and in the way they break into a system and keep the infection.
If we simplify a lot, the most lucrative banking trojan is the one we call “ZeuS” or “Zbot”, born in late 2005. Zeus, depending on who you are talking to, is one thing or another. Its story is long enough to cover code leakages, mutations, copycats… For this article, ZeuS is basically a philosophy and a template. A “template” because it allows, with a program, to create a banking trojan targeting bankings on demand, with its own syntax and some rules. A DIY kit with very advanced features. It is also a “philosophy” because of the way it steals, that may be considered a standard nowadays. ZeuS consolidated a style in banking trojan. What it does, and the basis of its success is (among mucho more things):
- It injects itself in the browser, so it can modify what the user actually sees in the screen. It injects new fields or messages and modifies the behavior or sends the relevant data to the attacker.
- If not injecting anything, it captures and sends all the outgoing https traffic to the attacker.
In this way and with this basic structure, ZeuS (as a concept) is alive and kicking for 8 years now. There is some more malware with different names, but fundamentally, they follow some of this style patterns.
 |
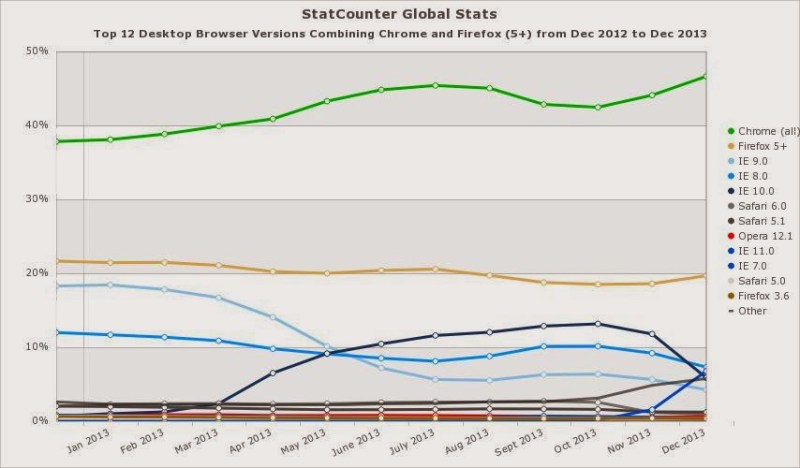
| Browser usage. 64 bits Chrome version is under developing in Windows. 64 bits version for Firefox for Windows was even cancelled for a while. |
What are they investing in?
ZeuS has evolved technically, but maintaining same basic structure. Is there an “official” ZeuS branch? Yes, you can buy it, but there are forks and other variants that became standard. Some features appear from time to time and some group of attackers adopt, copycat or buy them.
Focusing on latest changes, the most significant observed are: Using TOR to communicate to Command and Control Servers and Zeus compiled directly for 64 bits. Although not seen “in the wild”, this improves dramatically ZeuS capabilities.
One of the weak points (and advantages, in a way) of ZeuS (and malware in general these days) is that it strongly depends on external servers. Once these servers are down, the trojan becomes mostly useless. To solve this, so far they have used dynamic domains, domain random generator, fast flux playing with DNS, bulletproof hosting… and all these techniques are ok but they result expensive. Using TOR and .onion domains gives them “inexpensive” strength. Shutting down this servers will be very difficult for the good guys, and easier for the attacker to keep than any other “resilient” infrastructure used so far.
On the other hand, creating a 64 bits native version requires some clarification. Today, most of Windows system are 64 bits. In this architecture, 64 and (most of) 32 bits applications (except drivers) can run without problems. That is way today most of programs are compiled for 32 bits, so they can run in XP (with a not very used 64 bit version) and any other Windows (mostly 64 bits). So developers create 32 bits versions for all of them to ease compatibility. So does malware. Today, even with a 64 bits OS, browsers are still 32 bits (even IE, that comes in this two flavors in latest Windows). The reason is being compatible with plugins and extensions that are still 32 bits. So, why creating a 64 bit version of malware? Just because they can. They are maybe experimenting right now, for the near future. In fact, the 64 bit version have been detected “inside” a 32 version. This means that, once infected, it uses one or another depending on the browser. They will find very few people using a 64 bits browser (Its says only 0,01% of desktops are using native 64 bits IE), but that few is a market they do not want to refuse to, and when it raises (browsers are making efforts to have native 64 bits versions that will end up imposing) they want their software to be ready.
There is maybe another reason. Using 64 bits versions makes them even more unnoticeable for sandboxes in antivirus companies. This is the first step for most of AVs that goes through this detection circuit: sandbox, and, if suspicious, deeper analysis and, if even more suspicious but not classified yet… manual analysis. XP is still very used as a sandbox. 64 bits version of malware will not work there, and will go probably as a corrupted file. But this depends much on their resources and the way they work.
What that this changes mean?
That banking trojan developers do not fear users and just a little bit the AV companies… Their only limitations are their own technical skills. If they want to, they can be even more proactive than any other industry. And that they want the whole cake of users with every single nickel they have.
Sergio de los Santos