February, the first time
It all started in February. ElevenPaths detected at least 32 apps that used an old known technique in the PC world, but not so used in Android badware. Between the simulated apps, we could find a fake Talking Tom (that was online for just a few hours) and a “Cut the Rope”. In this case they visited ads and porn websites and simulated clicking in the banners, so they got some benefit. This schema affects the data plan of the user, because the apps will keep on requesting pages in the background and the victim will not be aware. The gang or person behind was operating since December, uploading apps to Google Play, with the only intention of booting with the device and making GET requests in the background.
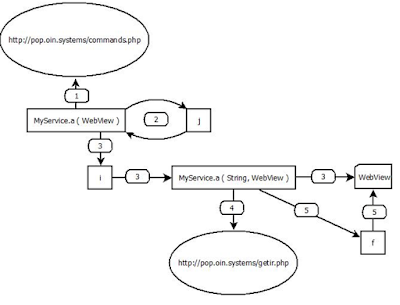
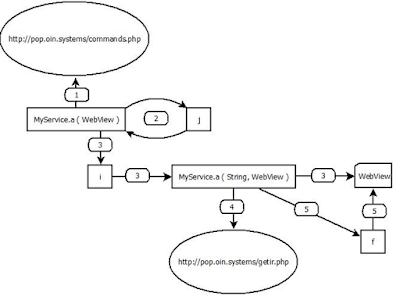 |
| App general schema |
We made a deep research on them, and published this article about it. The attacker used domains with real names. It is easy to find even their Facebook profile.
 |
| Name of the registrar, common for most of the domains used |
The first domain used for the attack still works as a “porn domain generator”. Since the beginning, it showed some preference for movie related apps, domains, etc.
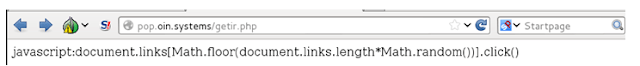
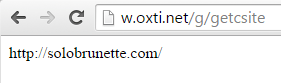 |
| Click F5… |
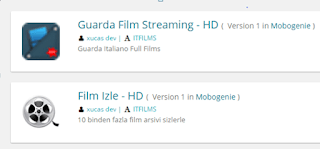 |
| Apps related to the attacker, found thanks to Tacyt |
April, the second time
Avast detected the attacker using again Dubsmash 2 as a fake app to spread these clickers. The way the apps worked were very similar, using the same JavaScript functions, part of the code, and Turkish addresses. But different enough to fool not only antivirus but Google Play again.
May, the third time
This time was Lukas from ESET, who alerted that the Turkish people were using same techniques and decoy (Dubsmash 2) to install clickers in victim’s devices. The attacker got a few thousands of downloads and installations. It even used the same domains as in February, where the infected devices got the information from.
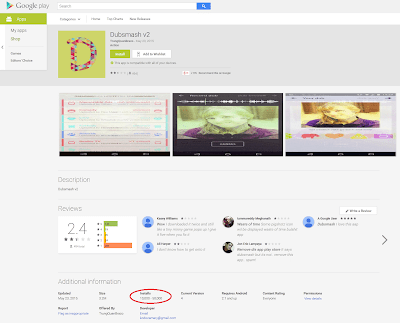 |
| Fake Dubsmash 2 used during May |
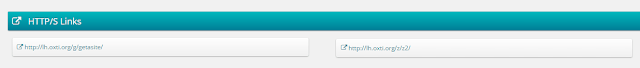 |
| Same domains as the first time, seen in Tacyt |
This time, Avast alerted again about the same people: Turkish, same “movies related” domains and apps, same Dubsmash 2 as a decoy, same network and JavaScript code. But again, different enough to fool Google Play and antiviruses. He never stopeed trying to upload apps during June, but during July it was more aggressive.
The attacker still uses the same structure as the offensive domains. Some of them seem to be compromised domains (peliculasgratishd.net?). These are all the domains (we do not show all the paths) related with this wave of attacks. They seem harmless, but this could change any moment from now.
- http://ynk.linuxum.com/
- http://kankalar.linuxum.com/z/z5/
- http://amas.europeanteenx.com/z/orap/
- http://sulale.hitgit.com/com.sulale.dubb/1.png,
- http://tranquockarafren.peliculasgratishd.net/g/getasite/
- http://kum.angelpinkgirls.com/z/z2/
- http://cinar.pussyteenx.com/z/z5/
- http://kamki.insfollows.com/com.nguyenngocjumraze.suuu/4.png
- http://phutanjocohare.mobilprn.net/g/getasite/,
- http://mebk.pantiescock.com/z/z2/,
- http://komidin.cumshotsex.net/com.komidin.cheatscrim/3.png
- http://rafta.girlstoyporn.com/z/orap/
- http://sulale.hitgit.com/z/z2/
- http://kendo.teenpornxx.com/z/orap/
- http://fet.asianpornxx.com/z/z5/
- http://pupa.romantictube.net/g/getasite/
- http://palasandoreki.filmsme.net/z/z2/
The attackers keep using the same Turkish name to register most domains. Code (inside and outside the app) keep on using some characteristics and formulas that are common enough to attribute the code to the same people.
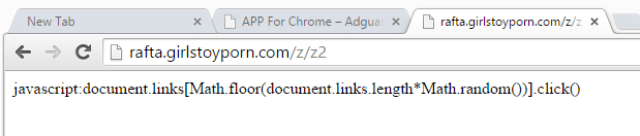 |
| Domain used in February (up) and domain used in July (down) |
Some of the files a are still available in Google Play while writing this lines.
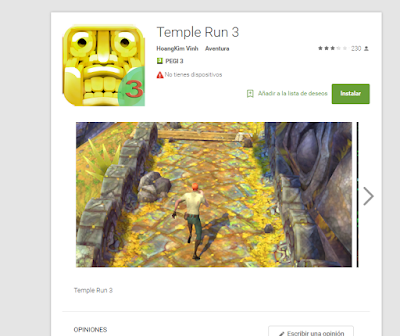 |
| One of the clickers simulating Temple Run 3, still online: https://play.google.com/store/apps/details?id=com.amas.ra |
These are some of the apps we have found during these last days so far (using Tacyt and a few clicks) that share the same characteristics. But, since February, they had to refuse to some “commodities” as for example, starting the app with the telephone, which limits the attack to the moment the app is opened… so that is why the attacker is trying to add some content to it lately.
- Amasra 1;com.amas.ra;f617515837ebe345a68904417d7823974e382e59
- Best : Dubsmash;com.kankalar.elma;99cc2f0ff000df5c2e856d40acac1b4dc72e9230
- Dubs Mash 2;com.sulale.dubb;459dc9198de2875017885d89e1c04c81301213b3
- Panita Kin;com.tranquockarafren.king;f320e227b9742527be37a1c03afe4f2689bb76f0
- Cheats for Boom Beach;com.kum.sal;36c4d4c0ca7c2d9e948daa32c20556709984fdba
- Cinarcik 1;com.cinar.cik;315c57bddee7a2ee5db54fb52215986bc23a9c93
- belki yanbak;com.nguyenngocjumraze.suuu;9b0e6c03338db95a86217ea298ae9a50c85c8217
- MayHada;com.phutanjocohare.may;9fe6f210fe5209c3d6d97800054e42d80d4e6966
- MayHayda;com.phutanjocohare.jat;84af3da99603e9d5586a2278d180d485c74d4068
- Cheats for Clash of Clans;com.kankalar.cheats;a0f000baa8246908bdce9feabc2f24530fd8afcb
- Man Kaptasi;com.phutanjocohare.conc;ed7ed72b9cf1de2cd67ce74d252be5aa7a2c0d35
- Cheats for Pou;com.mebk.adli;9d3e6747cf892a7bc7571b1b91da1d14061ad4bb
- Cheats for Criminal Case;com.komidin.cheatscrim;df5be5567eb7dc2ef8d6f96909ff6dfc29b37d8d
- Cheats for Hill Climb;com.rafta.chetashill;8d4a009bae65731f10adc0b7fbfb708918579e74
- Cheats & Trucos: Gta 5;com.sulale.chetastga;1741e985d4d204da73ee9f2a35622331fe7824c0
- Maps & Guide: GTA 5;com.sulale.cimmi;ed388d4dd304c695aba5794d089355febaeb80d8
- Followers for Instagram;com.nguyenngocjumraze.takip;5638df53b960a0d2b16f708bba8e46d4dc996f6d
- C l a s h o f C l a n s 2;com.kankalar.clash2;7552118b7e5f1ef3698579cc48121a6be37aa5f3
- Komidin;com.kendo.yako;0695c87554db4a10a7b38df49ecf03f6e20eb4db
- Fethiye;com.fet.hiye;49c37da0ca94536600cecd8290aba670164ba7a6
- Koday;com.pupa.yelken;2e2598c930a448217b6070d934e98735e4c44732
- Doganın Güzellikleri 2;com.palasandoreki.hsa2;961923bad0f1a986a142ef5916d57b053e6591ba
- Doganin Guzellikleri;com.palasandoreki.hsa;193e986d65249a8a04d596b9c13ecfdf0e3dced9
- Doganin güzellikleri 3;com.palasandoreki.hsa3;6dad78b0bae7210fcc9335ee671f4514becdb214
So, this is the fourth time the attackers modify the apps and get them in Google Play. But we have to consider that, once you are able to “fool the antivirus” just twisting code, this kind of badware is hard to detect, since the way the apps work is not that “suspicious” (“just visiting sites”) and the behavior can be easily “hidden”, for example, waiting for some events to start visiting porn sites.