|
| Figure 1: The six challenges of Big Data for Social Good |
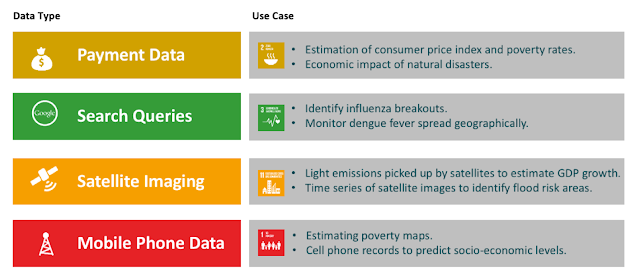
A data-driven approach can be taken for each and every one of the Sustainable Development Goals, using data to measure how the public and private sector are progressing, as well as helping policy makers to shape their decisions and have the greatest social impact possible. As we can see below, there are many different use cases that can be considered by organizations:
 |
| Figure 2: Big Data can support the SDGs |
However, many of the examples above refer to one-off projects and pilots and the real acceleration of towards these SDG’s will come from running these projects on a continuous basis with (near) real-time data-feeds to ensure stability and continuity for the next generation of social Data Scientists.
1: Privacy & Security
Data needs to be anonymized and aggregated. But will the anonymization process be good enough? Is it impossible to re-identify customers or users? Once the data is somewhere else, how secure is it? If it becomes a constant data feed, how safe is it?
2: Legal
For many companies, most of the relevant data is customer data. And although it is likely to be anonymized, aggregated and extrapolated, there is no full consensus on whether this is allowed or not. Organizations also have to face the challenges of there being a wide range of different Data Protection legislation in the different countries across their footprints.
3. Corporate reputation
Even if things are completely legal, professionals may still worry about public opinion and how customers may see things differently. What happens after a data breach, even if the use of data had a social purpose?
4. Big Data is the Key Asset
Businesses also have strategic commercial issues that they may struggle with. Many companies have only just learned that Big Data is a key asset, so may think why should they share this with someone else, even if for the greater good?
5. Competition.
Could the competition get hold of my data (asset) and make inappropriate use of it? How would I explain that one in the boardroom? The competition is tough and sending data to an external platform has most CSO’s concerned.
6. Cannibalization.
Does this use of data for social good cannibalize some of my external Big Data revenue? What if I jeopardize an existing business opportunity in order to carry out a Big Data for Social Good project?
 |
| Figure 3: Open Government Partnership Global Summit will take place in Paris 7-9 December 2016 |
it will encourager a wider range of companies to contribute
to the Sustainable Development Goals. And while OPAL is an interesting solution for the privacy, legal and reputation concerns, it doesn’t yet solve the strategic and business concerns mentioned above.
- Many international organizations are spending a significant part of their budgets on monitoring and achieving the Sustainable Development Goals, including The World Bank, United Nations, UN Global Pulse, UNICEF and the Inter-American Development Bank, While it may not be appropriate to charge commercial rates, it may be possible to have an “at-cost” model.
- Several philanthropists are donating large amounts for social purposes such as the Bill & Melinda Gates Foundation for gender equality, or Facebook’s founder, Mark Zuckerberg, who committed to donate €3bn to fight diseases.
- Many projects with a social purpose are a high priority for local and national governments. For example, generating a poverty index; anticipating pandemic spreads or reducing CO2 emissions in large cities. Governments are spending considerable amounts of their budgets on such projects and there is no reason why initiatives with a social purpose couldn’t also be charged for.
- Sometimes a freemium model works: pilots (or proofs of concepts) are done free of charge, but putting the project into production requires investment. Or, insights with a limited amount granularity (frequency and geography) are free of charge, but more detailed insights often have a bigger price tag.