One of the tools that the Islamic State has been using to spread its propaganda is the use of social networks. In the past they have shown how capable they are of expanding their capabilities to cover smartphones and mobile devices, but recently they have also opted for the development of browser add-ons in order to further facilitate access to their content.
Although Firefox extensions are mainly distributed by means of the official market run by Mozilla, the Amaq News Agency, identified as part of the Islamic State’s propaganda apparatus, is also distributing .xpi files in related websites. These files are compressed in .zip and renamed to a .xpi that contains the Javascript, CSS and HTML code that defines the behaviour of the extension.
About this extension, we have identified at least two different versions, 1.0.1 and 1.0.2, whose folder structure contains the same series of source and data files.
.
├── bootstrap.js
├── data
│ ├── safe-16.png
│ ├── safe-32.png
│ ├── safe-48.png
│ ├── safe-64.png
│ ├── safe.png
│ ├── unsafe-16.png
│ ├── unsafe-32.png
│ ├── unsafe-48.png
│ ├── unsafe-64.png
│ └── unsafe.png
├── icon.png
├── install.rdf
├── lib
│ └── main.js
├── META-INF
│ ├── manifest.mf
│ ├── mozilla.rsa
│ └── mozilla.sf
└── package.json
The most interesting files are three: package.json, install.rdf and the Javascript source file found at lib/main.js:
- package.json contains metadata and information about the extension like the name, the author, the licenses or the permissions required.
{
“name”: “amaq”,
“title”: “Amaq AR”,
“id”: “jid1-5Fs7iTLaaUaZBgwdar@amaq”,
“description”: “Amaq AR.”,
“author”: “Amaq AR”,
“license”: “MPL 2.0”,
“version”: “1.0.2”,
“icon”: “icon.png”,
“permissions”: {
“private-browsing”: true
},
“engines”: {
“firefox”: “>=38.0a1”,
“fennec”: “>=38.0a1”
},
“main”: “lib/main.js”,
“devDependencies”: {
“gulp”: “^3.8.11”,
“gulp-image-resize”: “^0.6.0”,
“gulp-rename”: “^1.2.2”
}
}
- install.rdf defines in the field em:targetApplication that the extension is thought to be installed in certain versions. In this case, it explicitly shows that it is valid for different versions of Firefox Browsers, including Firefox for Android (this is defined by the tag <em:id>{aa3c5121-dab2-40e2-81ca-7ea25febc110}</em:id> tagasda).
<em:targetApplication>
<Description>
<em:id>{ec8030f7-c20a-464f-9b0e-13a3a9e97384}</em:id>
<em:minVersion>38.0a1</em:minVersion>
<em:maxVersion>43.0</em:maxVersion>
</Description>
</em:targetApplication>
<em:targetApplication>
<Description>
<em:id>{aa3c5121-dab2-40e2-81ca-7ea25febc110}</em:id>
<em:minVersion>38.0a1</em:minVersion>
<em:maxVersion>43.0</em:maxVersion>
</Description>
</em:targetApplication>
- lib/main.js defines the code of the extension itself. In this case, it opens a new tab pointing to a given URL as shown in lines 107 and 108. The only difference between versions is the IP address shown in line 108.
var tabs=require(“sdk/tabs”);
tabs.open(“http://190.14.37.220/v/”);
Using the extension as a bookmark
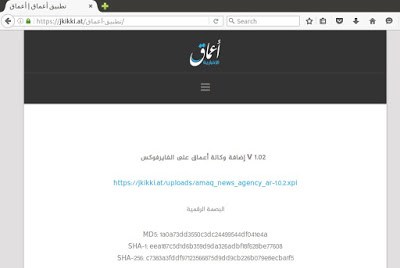
In the case of the first release of the add-on 1.0.1, the URL opened was hosted at 88.80.20.1 IP address (a non-accessible address linked to an internet services provider settled in Sweden) while in the most recent version this IP address is 190.14.37.220. This address, still accessible at the moment of writing this article, is linked to an anonymous hosting provider settled in Panama that runs a nginx 1.6.2. However, this resource seems not to be hosting the contents itself because if we access to this URL it responds a 302 Moved Temporarily code and redirects us to jkikki.at, the agency website. There, this Firefox extension can also be downloaded as amaq_news_agency_ar-1.0.2.xpi together with a hash of the file that would ultimately allow users to verify the legitimacy of the extension.
$ curl http://190.14.37.220/v/ -I
HTTP/1.1 302 Moved Temporarily
Server: nginx/1.6.2
Date: Tue, 10 Jan 2017 11:02:55 GMT
Content-Type: text/html
Content-Length: 160
Connection: keep-alive
Location: https://jkikki.at/
The referred website is hosting news in Arabic about Amaq and the Islamic State and is protected by Cloudflare making it impossible to know the real location of the systems used to serve the contents. By using this approach, banning the access to jkikki.at would not be enough to stop their propagation mechanisms considering that the application developer would only need to modify the Location field to redirect to the new domain in which the content would be hosted.
Identifying other affiliated websites
The structure of the URL found in the extension suggested the possibility of the existence of other domains. The tests conducted have returned new 302 responses that pointed to at least 6 other domains also protected by Cloudflare and whose content is also tied to the Islamic State. The details of the certificates used indicate recent validity periods as can be seen in the following table.
|
URL
|
Redirected domain
|
Language
|
Certificate valid since
|
|
http://190.14.37.220/b/
|
bibifm.at
|
Arabic
|
2017/01/10
|
|
http://190.14.37.220/f/
|
vosn.pw
|
N/F
|
2016/01/06
|
|
http://190.14.37.220/g/
|
baqiya.ga
|
German
|
2017/01/01
|
|
http://190.14.37.220/h/
|
halummu.at
|
N/F
|
N/F
|
|
http://190.14.37.220/t/
|
nikmat.gq
|
Bengali
|
2017/01/10
|
|
http://190.14.37.220/u/
|
vijestiummeta.ga
|
Bosnian
|
2017/01/05
|
|
http://190.14.37.220/v/
|
jkikki.at
|
Arabic
|
2016/12/31
|
Apart from this extension, there is no evidence of the existence of others with a similar behavior that point to the rest of domains. However, the recent creation of the certificates suggests that newer similar add-ons could be created easily by modifying only the URL of the original file to point to one of the URL shown before.
Registrant information and other metadata
Regarding the registry of identified domains, those that do not present special privacy protection measures have been registered email accounts using the tutanota.com encrypted email provider taking into account that the @keemail.me, @tuta.io, @tutamail.com and @tutanota.com (used to register a domain linked to the organization which is no longer used like jkikki.de) are different domains that make use of this service.
|
Domain
|
Registrant
|
|
bibifm.at
|
|
|
vosn.pw
|
|
|
baqiya.ga
|
N/F
|
|
halummu.at
|
|
|
nikmat.gq
|
N/F
|
|
vijestiummeta.ga
|
N/F
|
|
jkikki.at
|
|
|
jkikki.de
|
On the other hand, the rest of files identified in the extensions do not show too many details apart from some EXIF data found in the agency logos and icons. These files seem to have been edited with various Adobe products for Windows according to its metadata.
Assesment
The Islamic State has shown in the past that it has used the means at its disposal to massively spread its content in both, social networks and mobile applications. In this case, the use of a browser plug-in is another example of how the individuals linked to this organization are capable of adapting themselves to ensure the dissemination of content using not only a technological assets located in different countries, but tools and systems such as Cloudflare and various servers and methods to ensure the effectiveness of the difussion of their message.
Félix Brezo
Intelligence Analyst at ElevenPaths
Yaiza Rubio
Intelligence Analyst at ElevenPaths