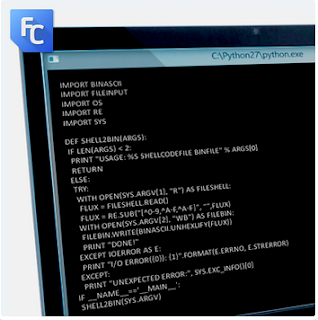
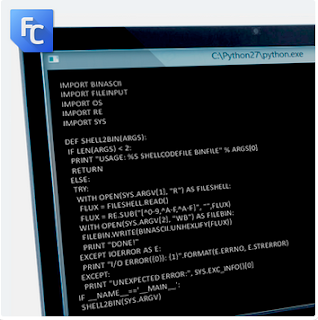
Script in powershell
With Powershell, retrieving the fingerprint of the certificate is quite easy. Just a few lines of code. Since most of the suspected machines will be Windows and all modern versions are able to use Powershell, this a simple solution. Just add the certificate fingerprint you are searching for in your computer, tell the program where to start from, and that is all.
To use it, just create your txt file with some fingerprints. For example, these are the fingerprints for the certs used in TheFlame (2012) and WildNeutron (2015) operations respectively.
1D190FACF06E133E8754E564C76C17DA8F566FBB
0D859141EE9A0C6E725FFE6BCFC99F3EFCC3FC07
We have uploaded the code to our Github. Whatever good idea you may have to improve it, just share it with us in our community.
Please note this is “quick and dirty” code with both practical and educational purposes.