|
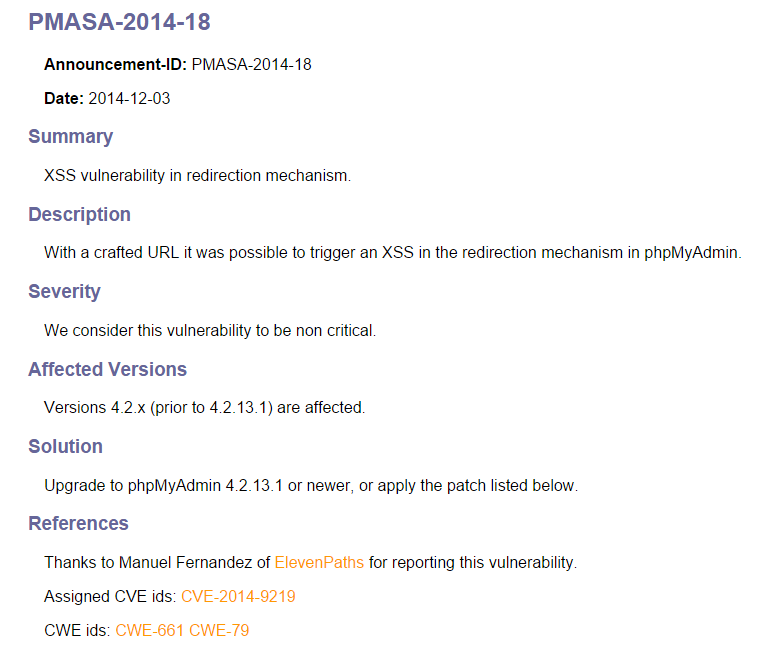
| Vulnerability and fix announce |
PhpMyAdmin security team has reacted promptly and in just three days they have fixed the problem and released a new version. The vulnerability (currently exploitable in any version previous to 4.2.13.1) relies in a bad filtering in the “url.php” file. The function htmlspecialchars was being incorrectly used.
The figure below shows the applied patch where htmlspecialchars function is replaced by PMA_escapeJsString.
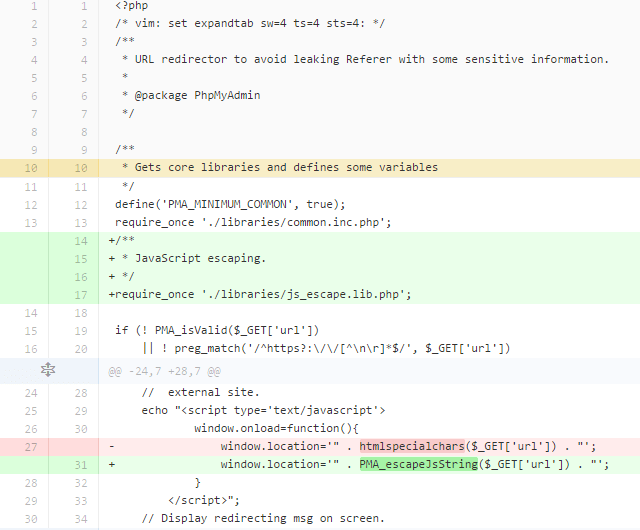 |
| Commit 9b2479b7216dd91a6cc2f231c0fd6b85d457f6e2 with the fixing line |
Just filtering HTML special characters, its exploitation was trivial. Besides, it was possible to bypass anti-XSS protections in browsers, because the injected code was reflexed into a “script” tag. This kind of vulnerabilities are very common in web applications, and allow different attacks, as obtaining session cookies, as shown in the figure below.
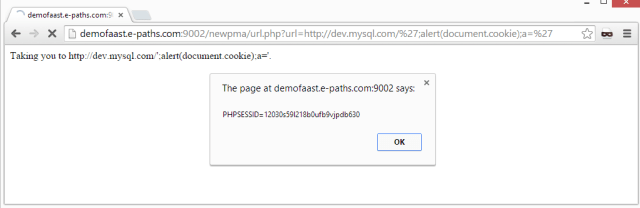 |
| Exploiting the vulnerability |
If you are using PhpMyAdmin, it is recommended to update as soon as possible to latest version (4.2.13.1) or applying the patch available here. Besides, we recommend using Faast that, of course, already detects this vulnerability.
Finally, remember we have a Latch plugin for PhpMyAdmin. All the information about how to install it, is here.