During the time we’ve been working in ElevenPaths we’ve faced many kind of events internally, buy one of the most exciting and awaited is the birth of Latch. It’s a technology of our own that has been invented, patented and developed by our own team… and, at last, exhibited to the world. We’re proud of the work that has been done and we needed to tell about it. Finally we can do so. This is Latch.

We think that users do not use their digital services (online banking, email, social networks…) 24 hours a day. Why would you allow an attacker trying to access them at any time then? Latch is a technology that gives the user full control of his online identity as well as better security for the service providers.
Latch, take control of when it’s possible to access your digital services.
Passwords, the oldest authentication system, are a security problem that we have to deal with every day. Second factor of authentication, biometry, password managers… We haven’t found yet the ultimate solution for the user not to depend on simple passwords, reusing them, or writing them on a paper. Latch isn’t that solution, either. Even advanced users that use good password practices are exposed to their passwords being stolen. Malware that focuses on credentials thievery are very “usual” since long ago. But even the most cautious users may have their passwords stolen by attackers if a third party’s database is hacked and exposed. Latch isn’t a solution for this problem, either.
Latch doesn’t replace passwords, but complements them and makes any authentication system stronger.
Latch’s approach is different. Avoiding authentication credentials ending in wrong hands is very difficult. However, it’s possible for the user to take control of his digital services, and reduce the time that their are exposed to attacks. “Turn off” your access to email, credit cards, online transactions… When they’re not being used. Block them even when the passwords are known. Latch offers the possibility for the user to decide when his accounts or certain services can be used. Not the provider and, of course, nor the attacker.
Latch’s approach is different. Avoiding authentication credentials ending in wrong hands is very difficult. However, it’s possible for the user to take control of his digital services, and reduce the time that their are exposed to attacks. “Turn off” your access to email, credit cards, online transactions… When they’re not being used. Block them even when the passwords are known. Latch offers the possibility for the user to decide when his accounts or certain services can be used. Not the provider and, of course, nor the attacker.
Latch makes it possible to control your services even if an attacker has stolen the user’s password, credit card or any other service that needs authentication, making it impossible for the attacker to use the stolen data in that service out of a defined time interval. In other words, (by just pushing a button) it’s possible to make the authentication credentials for any service valid only for that very moment when the user needs to introduce them on the system.
Latch’s scheme
Even though we’ve talked about passwords, Latch is actually a service to protect service provider’s defined processes for interacting with the end user. The background and uses that may be given to these processes are independent of the protection layer that Latch provides.
The main idea of the structure of this protection is limiting the exposure window that an attacker owns for taking advantage of any of these processes. The user will decide if his service accounts are turned ON or OFF and even will detail the actions that can be taken from those services. This makes it possible to reduce in time the possibilities of an attack, associating an external control to every operation. The service provider requests Latch for the user-defined status of a certain operation for a defined time.
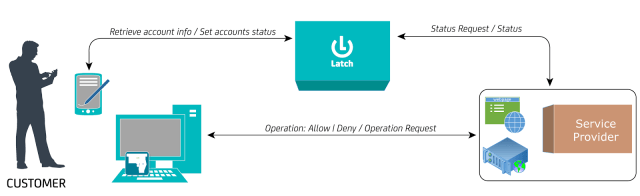 |
| Latch’s general work scheme |
In this figure, a client that tries to execute an operation from a service provider obtains confirmation on whether the operation has been allowed or denied.
The configuration of an operation’s state is made through an alternative channel (and considered more “secure” than the regular device), so any attempt to access an operation blocked by the user may be identified as an anomaly. Such an anomaly could imply that the user trying to access the blocked operation is not reality who he’s claiming to be and a possible fraud attempt is identified.
How it works in practice
How it works in practice
The user will only need a smartphone to “activate” or “deactivate” the services paired with Latch. To do so, he or she will need to:
- Create a Latch user account. This account will be the one used by the user to configure the state of the operations (setting to ON or OFF his services accounts).
- Pairing the usual account with the service provider (an email account or a blog, for example) that the user wants to control. This step allows Latch to synchronize with the service provider and to provide the adequate responses (defined by the user) depending on which operation is tried to be used. The service provider must be compatible with Latch, of course. This allows the users to decide whether to use Latch or not. Latch is offered but not imposed.
Latch for the service providers
Latch allows the users to configure the access to their services, and to accomplish this, the service providers need to integrate Latch in their systems. We’ve programmed different SDKs in many different languages (.NET, PHP, ASP…) and we’ve created plugins for already existing platforms such as WordPress, PrestaShop, Drupal and Joomla. The webpages using these platforms are able to offer Latch to their users quite easily… so the users deciding to use the service may take advantage of Latch also very easily.
The integration is easy and straightforward, giving the service provider a great opportunity to improve the security offered to its users, and therefore, their online identity.
And that is not all…
Latch offers more ways to protect users, their credentials, online services and online identities. We will introduce them soon. Stay tuned.






