Faast teams have been working all day long to add a new plugin to our list of detected vulnerabilities. There has been found a new security problem in TLS protocol that allows to force the use of insecure 512 bits keys during Diffie-Hellman exchange. The use of such a short key, plus a bad practice in servers using over and over basically the same 512 bits primes, allows an attacker to break into most of supposed secure connections. This vulnerability, reported today, is known as Logjam and could affect 80% of TLS connections.
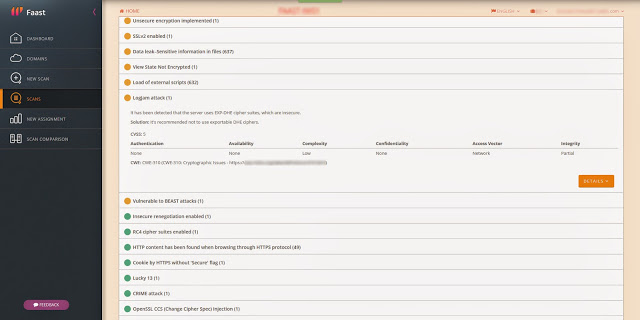 |
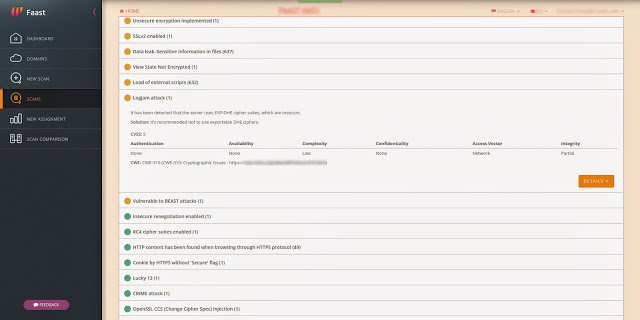
| Detection of Logjam included in Faast knowledge base |
After analyzing the vulnerability, our developer teams in Faast have added to our knowledge base a plugin to detect Logjam that, after going through QA process, has been released tonight. All our persistent pentesting clients will be getting security warnings related to this problem if it is detected in their infrastructures.
Referencess:
– Logjam description
– Imperfect Forward Secrecy: How Diffie-Hellman fails in practice [PDF]
– Logjam description
– Imperfect Forward Secrecy: How Diffie-Hellman fails in practice [PDF]