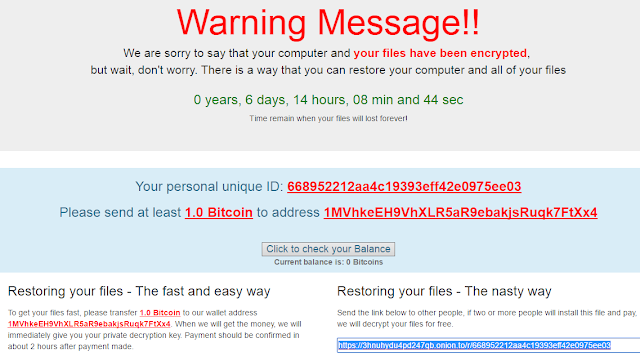
 |
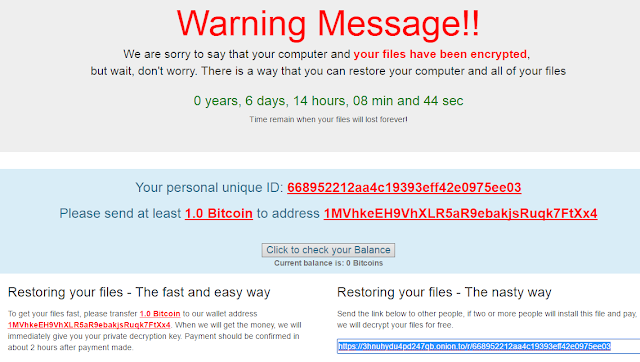
| The “easy” way and… the “nasty” way |
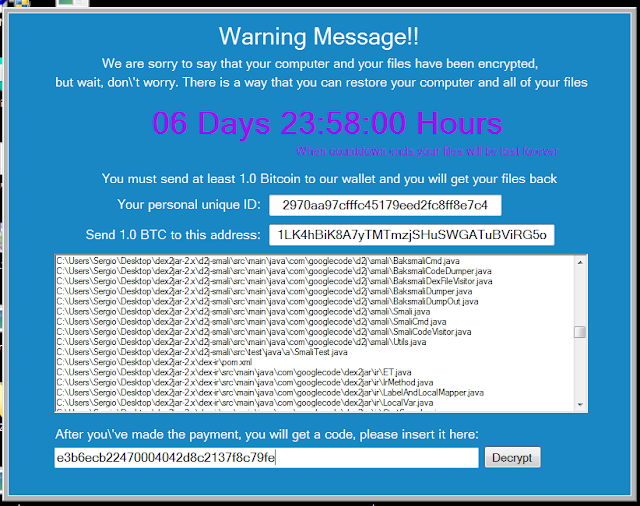
Apart from what has already been commented on this new version, we focus on the most interesting aspects of the evolution that we, at ElevenPaths, have analyzed. The basic functionality is as usual: a lot of files are encrypted depending on their extension, and a ransom of 1 bitcoin is requested (above the average that is usually demanded). What this ransomware does for the first time is to offer two ways to decrypt the content: the “normal” way, in which a ransom is paid, and the “nasty” way (so they call it), in which if a link to an executable is sent to two people and they get infected and pay, you will be given a “free” code to decrypt your content. A diffusion “Refer-a-friend plan” in which the attacker “ensures” two infections for the price of one, and a more effective dissemination method, since the victims chosen by the infected user will always be more predisposed to execute the link from an acquaintance. Another option is to pay (alleged condition for the “discount”). It is also important to note that the ransomware appeals to the sensitivity of the victim, stating that the money will go to a good cause: alleviate the effects of the Syrian war. It is called “popcorn” because the first version used the popcorn-time-free.net domain, although the latest versions do not.
 |
| Appealing to the sensitivity of the victim. They also lie when they say that there is nothing to do and that only they can decrypt the data. |
Technical aspects
How does this ransomware work at a technical level? It has been developed by an independent group without following the guidelines of the “known” families, and therefore, is not very developed yet. Apart from the versions analyzed by MalwareHunterTeam, at ElevenPaths we have had access to the new samples. These are some interesting aspects that we have noticed.
The program is written in C# and needs .NET4 to run. The executable is created “on the fly” for each infected user, with a unique ID code inserted for each victim. Interestingly enough, all variables are “embedded” in the code, and it is created on the server side. In addition, it does not follow the usual pattern of professional ransomware in which each file is encrypted with a different symmetric key and then this key is encrypted with asymmetric cryptography. On the contrary, all files are encrypted with the same symmetric key. From here, knowing the password is a matter of analyzing the code of the executable.
The password
If we disassemble the code with, for example, ILSpy we can see the line containing the password in base64. A quick decode will allow us to get the password and the data back. We have not created a specific tool to do this, as it is more than likely that the attacker quickly changes the strategy and also, for now, this malware does not seem to be very advanced or widespread (if someone is infected, please contact us). In fact, the day before the password of its first versions was always “123456”.
As mentioned, the password is supposed to be (along with all other variables) embedded by the server at the time the executable is created. After the analysis we have conducted, it turns out it is an MD5 hash of which we still do not know what it responds to. The MD5 hash is triply encoded with base64 in the code.
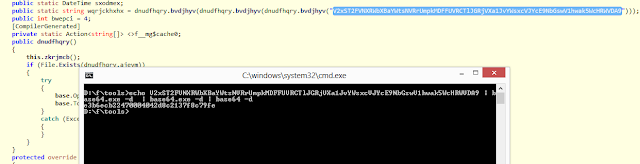 |
| Partof the code where the password appears and how to decode it in base64. Click to enlarge |
The result of the decoding is the password that can be entered in the corresponding dialog to decrypt the data without having to pay at all.
The rest of the code is sometimes messy, although it seems they are working day by day to improve it. For example, the salt in the cryptographic function is not random. This, which in any other circumstance would allow a precomputed dictionary attack, really does not have much effect here (the password is not in a dictionary, it is a hash), but it gives us an idea of the little cryptographic value that this ransomware has.
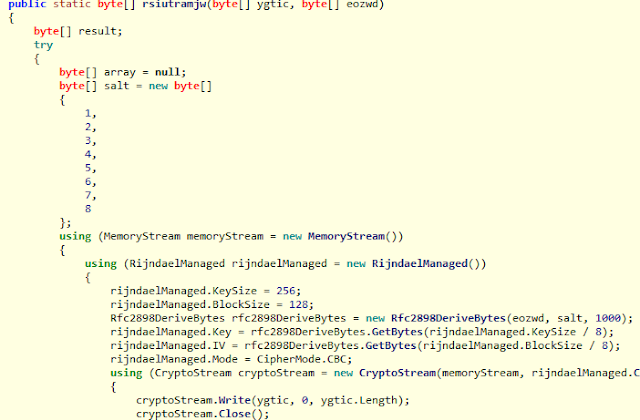 |
| A not very useful salt (12345678), although it is not very important here. |
HTML code
The HTML code that is displayed to the victim forms a very important part of this malware. It is also embedded encoded in base64 in the code. In it we can see that a verification is conducted using the APIs of the Blockchain.info (misused, it encloses the wallet in quotation marks) in order to know if the payment has been made and if it is validated in the blockchain. It uses Satoshis, which are a fraction of a bitcoin.
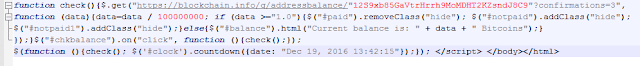 |
| They misuse the API of Blockchain.info, although later they correct it |
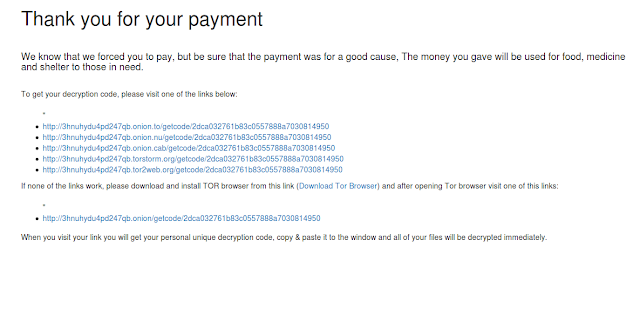
If so, they display some URLs hidden in JavaScript that are supposed to give access to the decryption code, and hosted in the Tor network. This protection (using a “hide” class) is ridiculous. When we access the URLs, the truth is we cannot see any decryption code (we guess that because they are still in the trial stage).
 |
| They are supposed to provide you with the decryption code when you pay and visit those URLs, but it does not look like it. |
Refer-a-friend plan
What stands out the most about this is the “nasty way” to decrypt the files. Allegedly, if you send the executable link to two acquaintances and they pay, you will be given the unlock code. It is a very smart way to get a fast diffusion, but we think it is not true. The code does not contain any instructions to verify that this happens automatically. Unless all intelligence runs from the server side (which we doubt), we cannot guarantee (nor have we technically proven that it happens) that this is so and, therefore, this is more likely to be just a hoax to spread more malware. In fact, the generated executables do not contain information about who has recommended them, only the fact that they have been created under a URL that does indeed contain the ID of the initial victim. But looking at the entire system, its poor programming, unfulfilled promises, threatening countdowns that in the end do not erase a thing and the unstable infrastructure and “craftsmanship” in general, Occam’s razor makes us lean to think that everything is false and that there is no mechanism to control this.
Remember that we have a tool with an approximation of proactive protection against ransomware that you can (soon) download from our laboratory.