A few days ago we published the cyber security report of the first half of the year, where you can find a special chapter about the threats in the OT world, also known as Industrial Control System (ICS), taken from the metahoneypot that the innovation and laboratory area deployed in C4IN, which is called Aristeo.
In the 24 hours prior to writing this article, Aristeo had detected nearly 3’000,000 cyber security events targeting these infrastructures. In the last six months we have witnessed how critical infrastructures, which base their operation on ICS, have been front page news around the world, with cases such as the Colonial Pipeline Ransomware, the detection of bugs in Schneider Electric systems, implications of the SolarWinds case in industrial environments… amongst others.
Why are the incidents so serious?
The world of ICS has migrated rapidly towards digitisation, Industry 4.0 has advanced with the pandemic by leaps and bounds and is here to stay. However, not all changes have been made with the protection of this infrastructure in mind, nor have they taken into account that the protocols and connections they handle are not necessarily up to date or prepared to handle the traffic that is common in IT networks
This makes some devices much more prone to denials with a simple port scan or some HMI consoles have obsolete operating systems as they support the software for the DCS or SCADA they manage.
Another clear indicator of ICS’s cyber security weaknesses is the increase in vulnerability reports issued by CISA, which in July 2020 alone accounted for a total of 21 reports, while in the same month of 2021 there were 41 reports.
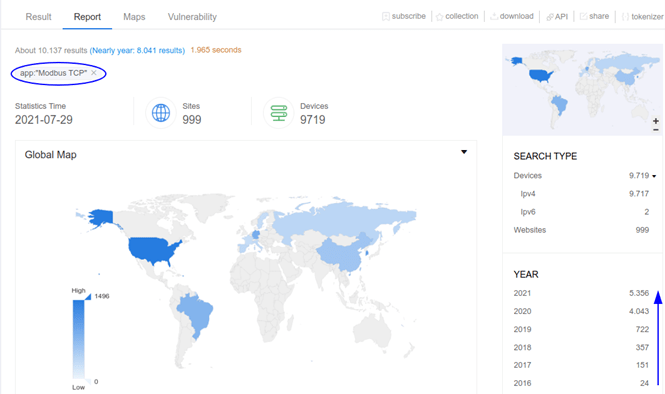
Another clear indicator of the lack of safeguards that have been in place during the pandemic for industry’s migration to digitalisation is the increase in detections of equipment with industrial protocols by Internet engines, as seen in the ZoomEye results.
Every action has consequences …
The sum of all these indicators of poor cyber security management has generated reactions from the different actors involved in the attacks, on the one hand it is clear that the criminal industry has started to direct its actions towards the industrial control sectors, although the history of ICS incidents is long and has very important cases in the last 12 years.
And it has also generated a reaction from states, which have seen how their countries’ critical infrastructures have been affected by these organisations, generating new policies and obligations for the operators of these infrastructures. Undoubtedly, the most affected country has been the United States, which is why at the end of July the White House issued a memorandum that obliges operators responsible for the functioning of critical infrastructure to improve the cyber security of their operations.
Yet is not the only country to have taken presidential action. Following a series of incidents, Australia has decided to implement improvements in state policies to reinforce critical infrastructure protection.
What kind of action should be taken …
Companies have already started to take action and look to the market for options to improve their cyber security posture in industrial control environments, as can be easily seen by how auditing firms have started to enter into commercial agreements with companies in the cyber security sector.
We at Telefónica are aware of the importance of this sector and the need to be at the forefront of cyber security, and for the last year we have been an investor in Nozomi Network. We have also created the C4IN innovation laboratory, launched in 2019, where several developments have been generated to improve industrial cyber security and where Aristeo, the metahoneypot for threat intelligence in the sector, has been created
This gives a clear action that with case studies contributes to the improvement of cyber security in industrial environments and allows to minimise the effectiveness of criminal actions that have increased towards this business sector.