- What’s going on with these “new” malicious adware families? How “new” are they?
- Are these different malicious adware campaigns somehow connected?
- Who has developed this adware campaigns?
In order to find the answer to these questions, the reported malicious adware families have been “squeezed” by Eleven Paths analyst researches using our in-house developed mobile cyber-intelligence Tacyt tool, to obtain more contextual information and the particular associated app “singularities” (technical or circumstantial app data that are “singular or unique” to a developer and/or application).
The above mentioned different adware campaigns have been analyzed and correlated on the basis of various application parameters, and the evidences obtained suggest us that:
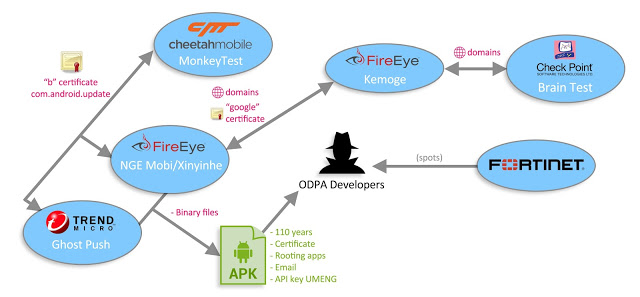
- The malicious adware family reported recently by FireEye (in September and October) seems to be related with the “Ghost Push” malware discovered by CM Security Research Lab and Trend Micro, as several clues regarding the links and associated certificate info included in the app point to the same developers, which in turn, seems to be related with the FireEye’s “Kemoge” called adware family as well.
- The “Brain Test” malware app reported by CheckPoint contacted a server domain included also on the “Kemoge” adware family sample.
- The aggressive adware discovered apps have had some versions in Google Play in early 2015, by a developer that produced aggressive adware as well.
Taking into account the several obtained “singularities” and hints, it seems that this adware or malware may all come from a single root, probably the known Odpa or Opda (it depends on the antivirus engine) creators (a known adware and infostealer) that may be the predecessor of these malicious adware families.
 |
| Brief research schema |
Squeezing the Apps
Here we expose a few details of a much deeper analysis that you may find complete in a link below.
As shown in one of the FireEye reports the attackers have repackaged popular apps and inject ed malicious logic and ad components into the apps. The malicious adware iterates some domains and posts data once a connection is established. Searching with our Tacyt tool for the specific domains used by the malicious adware as indicated by the FireEye team, our analysts have found 12 different apps (some from the report itself, some from “Kemoge” samples). One of them, with “com.android.camera.update” package name, to be related to another (and supposed different) described mobile attack dubbed “MonkeyTest” by Cheetah Mobile on September 18th, 2015.
Searching for the com.android.camera.update app (from CM report), it reveals that this app uses a certificate singularity shared with one of the FireEye is reporting as downloaded by their samples. It shares the word “dashi” as well in the package name. There are even some specific strings in the code, which are shared between samples from all the reports.
It seems that some of the apps related with the developers were uploaded to Google Play back in late December or January. Searching with Tacyt for some specific binary files inside the apk, it brought us to some apps on Google Play which have been removed last January from the market.
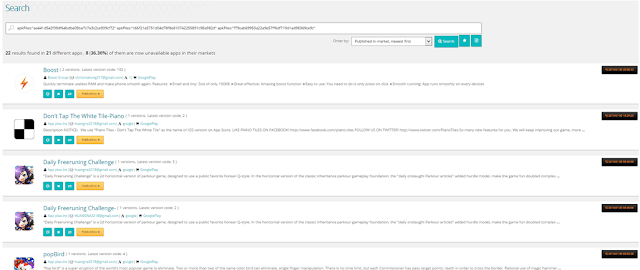 |
| Apps sharing very specific binary files |
A curious thing is that most of them share this application permission, which is not very common (32 out of 4.5M apps): android.permission.ACCESS_MTK_MMHW.
Searching for certificates with those particular characteristics and for apps removed from Google Play the exact same day (which is supposed to be when Google discovered the fraud and cleaned the market), Tacyt obtained some evidence of related bands, like this particular UMENG ApiKey, as shown on the picture below:
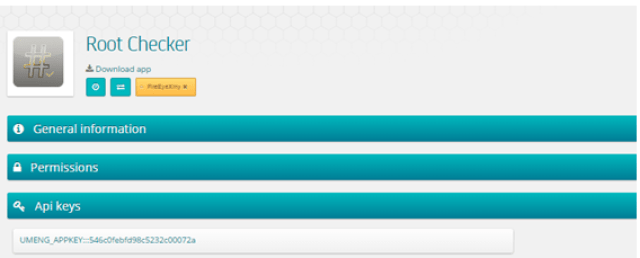 |
| Shared UMENG Api Key |
This UMENG ApiKey has been shared with only a previous version of “Root Checker”, removed from Google Play on 27th, December, 2014 and from “OPDA” developers that claim that their developer web is www.dashi.com, which in turn, is related to a previous package name used in NGE (Xiny) attack. And there are even more connections between the word “Dashi” and OPDA developer. OPDA developers may be behind Odpa/Opda adware famlily, found in summer 2014.
On the other hand, CheckPoint reported that some of the domains found inside “Brain Test” malicious app seems to be present in “Kemoge” adware family as well:
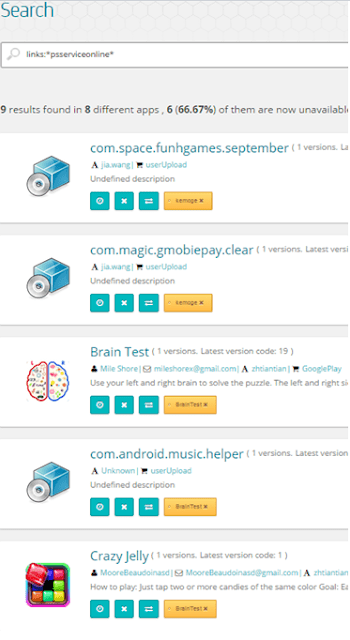 |
| Sharing specific domains |
Conclusions
Tacyt’s powerful engine enables the analyst teams of the organizations to easily evaluate and correlate the application and its circumstances: when, who, what and where.
Using Tacyt our analyst team has been able to obtain further evidences that suggest a relationship between several reports, and confirm that some of aggressive apps discovered had a version in Google Play in early 2015. The evidences suggests that this supposed different families of malware, may be just the same Chinese band (because of the infrastructure, domains, topics, files, etc. they use) evolving the same idea about serving aggressive ads, rooting the devices, sending commands and installing new packages.
We assume this because of the several hints that join the families: domains, dates, permissions, names, certificates, resources, etc. They started their activities maybe in late 2014, using the OPDA “brand”, trying to introduce malware in Google Play and legitimate apps as well. Later, they have evolved with new techniques, from “Xinyinhe adware”, that seems to be just a variant of “Ghost Push” to “Brain Test” which seems some experiment before they got to “Kemoge”. It seems that this Chinese gang is evolving techniques and creating more effective adware that are not able to spread via Google Play anymore, but third party stores. Anyhow, it seems that they use Google Play to serve “less aggressive” adware.
Disclaimer:
This whole report has been done without code analysis and with the minimum information provided by the blog post mentioned above. Taking into account more samples, relations between all the samples are even stronger. A further analysis of all the data collected (emails, links, strings, etc) from all the apks related, may guide us to a more accurate attribution.