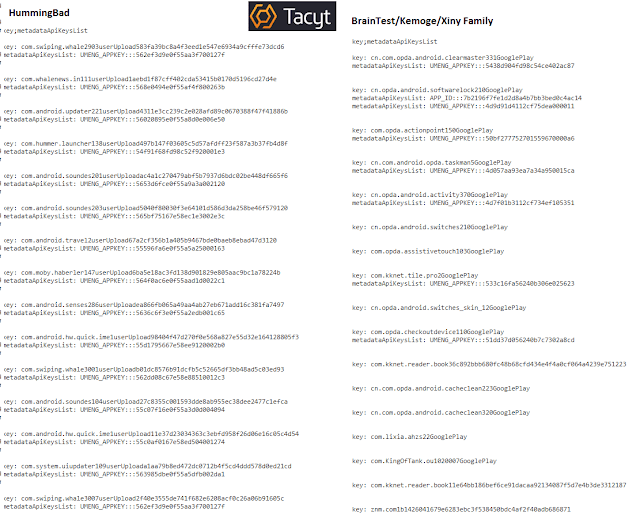
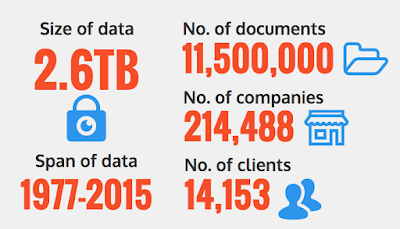
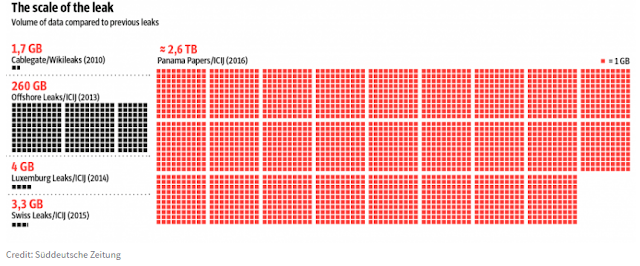
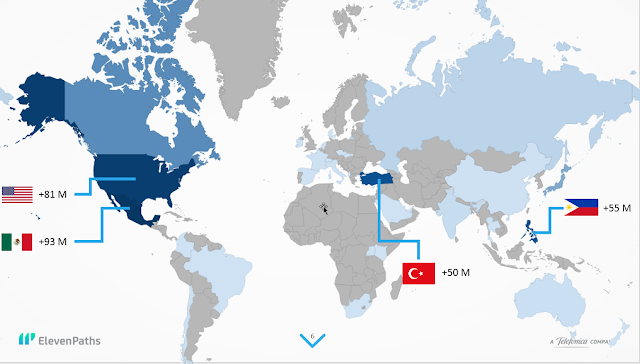
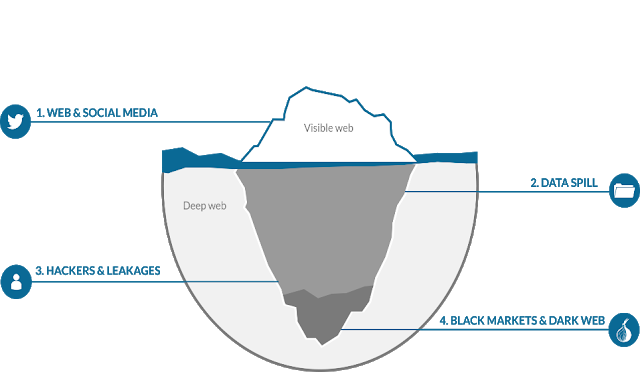
Telefónica welcomes two relevant milestones that have taken place in Brussels during the last days in order to foster the European cybersecurity strategy to avoid incidents that can undermine consumer confidence and cause major economic damage to European business and the economy at large. Cybersecurity and the fight against cybercrime has turned into one of the political priorities for the ICT sector in the EU and Telefónica is ready to play its part.
On July 6th, the European Parliament Plenary voted on the Directive on Network and Information Security following the adoption by Council in last May.
The NIS Directive is the first EU wide legislation on cybersecurity ever and culminates a long process of negotiations between Parliament, Council and European Commission.
Once the Directive enters into force (on the twentieth day after it´s been published in the EU Official Journal in August) Member States will have 21 months to transpose it into their national laws.
For the first time, NIS Directive creates a legislative framework that will also apply to some digital services, leveling the playing field and establishing harmonized requirements regardless of whether the providers of these services are based in the EU.
The three pillars of the Directive aim at:
- developing of national capabilities
- cooperating among national Authorities
- establishing specific security obligations and notification requirements for operators of “essential services” (traditional critical infrastructures) and providers of “digital services” (such as Cloud providers, online market places and search engines)
One day before the NIS Directive was voted by the European Parliament, on July 5th, the Commission adopted a Cybersecurity Package composed by a decision establishing a contractual Public-Private Partnership on Cybersecurity expected to trigger €1.8 billion of investment by 2020 and a Communication on a Competitive and Innovative Cybersecurity Industry, setting the basis for a “industrial policy” on Cybersecurity.
The cPPP is basically a contract between the Commission and the European Industry with a commitment to co-finance specific lines of research. Pedro Pablo Pérez, ElevenPaths’ CEO and Telefónica Global Security Managing Director, has been appointed as member of Board of Directors and also Partnership Board of European Cybersecurity Organization (ECSO), the association that will implement the cPPP.

Telefónica is the only telco operator that has been selected to occupy this relevant position. This reinforces our commitment to enhance Digital Confidence of customers, citizens and businesses, in line with Telefónica’s positioning in Public Policy and our willingness to engage with the Commission in realizing the vision for a secure and trusted online environment in Europe.
The main goals of the Cybersecurity cPPP are:
- to improve industrial CyberSecurity capacities and digital autonomy of the EU, by promoting trust and security in digital services and networks in response to global cyber threats, while respecting EU values (Fundamental Right to Privacy)
- to stimulate developments of EU industrial and technological resources to overcome
- existing gaps in EU technology and online services
- existing barriers for the achievement of a real Digital Single Market for Cybersecurity products and services
- with the ultimate goal of contributing to a strong European Cybersecurity Industry
As we can see, there is a firm commitment manifested, now it´s time to move from words to deeds because nowadays the digital world goes much faster than the physical. There is no time to waste.
» The original post is based on Telefonica’s Public Publicy Blog and written by Andrea Fabra
“European Cybersecurity Strategy: Telefonica’s support”