You can now download the full report about Insecurity in the Internet of Things carried out by ElevenPaths’ Analyst Team. It`s available at ElevenPaths web.
Summary
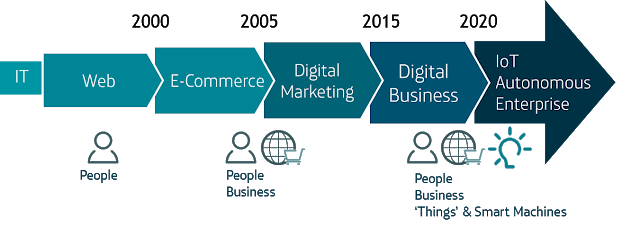
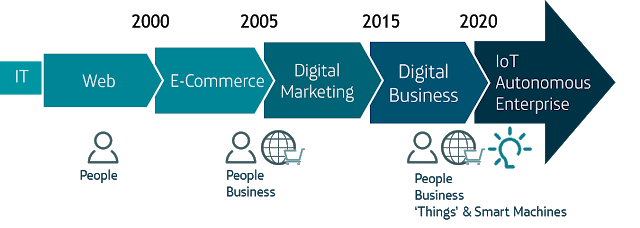
In the past six months potential insecurity within the Internet of Things (IoT) has been regularly making news headlines, from hacking planes, cars, or baby monitors, to Smart TV’s insidiously listening to and broadcasting unencrypted conversations across the internet. A September advisory issued by the FBI indicated that they too had concerns over inherent security flaws in the implementation of the IoT and warned over the potential opportunity offered to cyber criminals. While to many such a warning may seem premature given the current market penetration, the IoT is currently at a peak of expectation and anticipation, essential to driving the concept forward. In enterprise the IoT is seen as an integral part of the blueprint for developing from the digital business model of today to the digitisation of the entire value chain, and in the consumer space ‘wearable’ adoption is rising rapidly. However advances in edge computing, networks, big data and analytics are still required for this truly disruptive technology to shape the future; and although widespread implementation is likely to be 5-10 years away, not addressing security flaws now will only compound the problem for an IoT connected world.
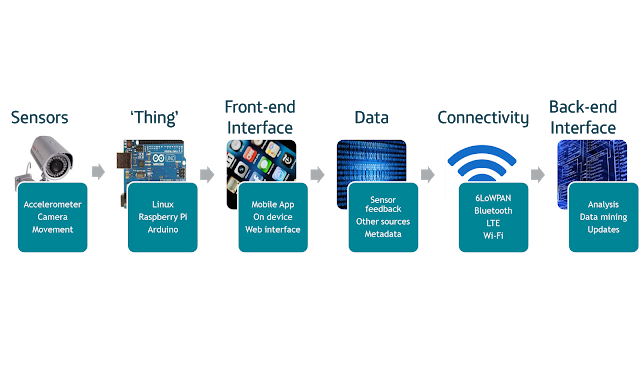
Such scope ensures that IoT should not be thought of as just a ‘Thing’ in itself; it is a collection of technologies integrated and presented to provide specific and vastly diverse applications. However in terms of manufacturing, a rapid development lifecycle is producing devices that are ‘always-online’ and often possess inherent restrictions on security measures due to size and cost; research that has indicated that as many as 70% of commonly used IoT devices contain significant vulnerabilities. Although maintaining consumer trust, regulating the quantity and nature of data to be collected and transmitted, and also tackling end-user behavioural traits likewise provide complex challenges. At this nascent stage in the lifecycle, focus on securing it is often disproportionately weighted on the end device, forgetting that it is merely a component of a larger eco-system that is only as strong as its weakest link.
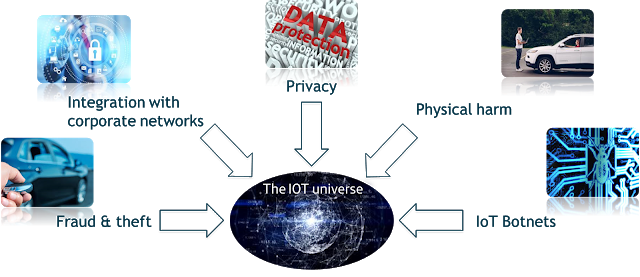
Methods to subvert these technologies will depend both on the manner in which they mature, and how security is implemented on often exposed devices. Worryingly, the early indications are that the network, application and cloud security lessons of the past 20 years have often been forgotten by existing technology vendors, and not yet learnt by manufacturers pushing into a new market. While risk exposure from IoT vectors is likely to remain low in the short term for most enterprises, but risk assessments may prove it is higher than first thought. The uptick in reflective DDoS attacks in H2 2014 and composition of the ‘Lizard Stresser’ botnet already points towards the effect of an insecure IoT being maliciously re-purposed. Unanticipated information leakage from the extended IoT ecosystem may also compound the problem of data aggregation from both consumer and enterprise sources, enabling cyber criminals to unite disparate data sets for a wide range of malicious goals.
The concept of security by design must be given a higher priority in order to avoid security flaws being compounded as the IoT matures, and adopters should be alert to IoT integration in a less mature, loosely regulated environment, or risk costs spiralling later. Core principles of data, application, network, systems and hardware security remain applicable but the complexity is higher and measures must be more careful not to work against the user. The IoT will be transformational, disruptive technological movement, but carries a spectrum of risks that affect more than just the IT department.
ElevenPaths’ Analyst Team