Evil Foca was introduced in early April, as a tool to make local networks pentesters and auditors life easier. In a simple way and with a very simple interface too, it allows to automate different attacks, showing how insecure local networks may be “indoors”. Among them:
- Man In The Middle (MITM) over IPv4 with ARP spoofing.
- MITM over IPv4 with DHCP ACK injection.
- MITM over IPv6 with Neighbor advertisement spoofing.
- MITM over IPv6 with SLAAC attack.
- Rogue DHCPv6 attacks.
- DoS (Denial of service) over IPv4 with ARP spoofing.
- DoS over IPv6 with SLAAC DoS.
- DNS Hijacking.
Even more, during DEF CON 21, celebrated a few days ago in Las Vegas, a new version of Evil FOCA (DEFCON Edition) was introduced. The main feature added for this version is the implementation of a full automated Web Proxy Auto-Discovery attack.
This presentation, quite successful according to some witnesses, showed live what you can get with IPv6 (enabled by default in Windows) MITM attacks, and how easy it is to leverage protocol vulnerabilities with Evil Foca.
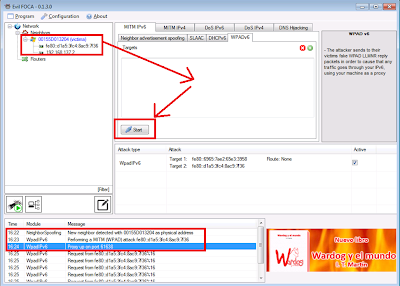 |
| IPv6 attacks with Evil Foca. New version does not include ads |
Slides are available here:







